Task 1 Web App Testing and Privilege Escalation
Deploy the machine and connect to our network
Easy enough I got this!

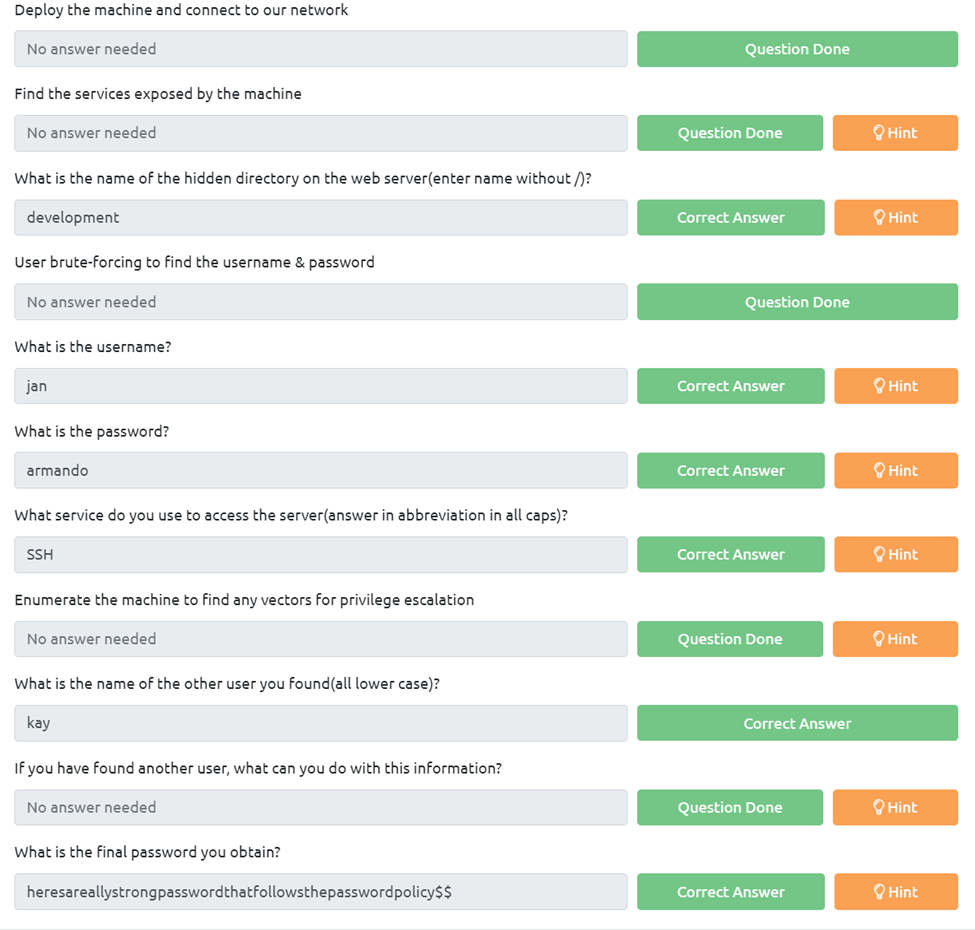
Find the services exposed by the machine
For this I am going to run Nmap -sV -v (targetip)


What is the name of the hidden directory on the web server(enter name without /)?
For this were going to use gobuster with, gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u 10.10.193.196. From there we can see a /development directory. If we go there we see two .txt documents with some hints.
User brute-forcing to find the username & password
What is the username?
To start this we can run enum4linux -a 10.10.193.196 | tee enum4linux.log and look through the log file and see that we have two users


What is the password?
For this we can brute force it using hydra -l jan -P /usr/share/wordlists/rockyou.txt ssh://(target ip). Since we know that ssh is running from our nmap that is where that comes from. After letting it run we do get a password for jan.

What service do you use to access the server(answer in abbreviation in all caps)?
SSH is what is typically used to access a server.
Enumerate the machine to find any vectors for privilege escalation
To do this first we need to get linpeas if were using the attackbox we can do so by using
$ mkdir linpeas
$ cd linpeas
$ git clone https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite.git .
Next we need to get this on our victims computer to do so we will use root@ip-10-10-113-209:~/linpeas/linPEAS# scp linpeas.sh jan@10.10.193.196:/dev/shm Then from our victims computer we will need to make it executable with chmod +x linpeas.sh and then we just invoke the ./linpeas.sh | tee linout.txt
What is the name of the other user you found(all lower case)?
We can just refer to the above found user list.
If you have found another user, what can you do with this information?
What is the final password you obtain?
For this we can look at the files we can access and we can see kay has a ./ssh/id_rsa key that we can read. So let’s copy it and now if we nano that into a file on our attacking box. Next we can try to ssh into the box but it needs a passphrase so we can attempt to brute force it with john. But first we need to use ssh2john.py to get a hash then we can use john with rock you to crack it.

After john has done his magic we can try to ssh -i (id_rsa fil) (username)@(victim ip). And finally we can just cat the pass.bak file for the final flag.