
Task 1 What will this room cover?
I’m ready to learn about encryption
Task 2 Key terms
No we will not complain and through the reading we can see passphrases protect keys.
Task 3 Why is Encryption important?
Task 3 Why is Encryption important?
Through the reading, we can deduce what SSH means and also that web servers use certificates to verify identity, also anything pertaining to credit card handling falls under the PCI-DSS.

Task 4 Crucial Crypto Maths
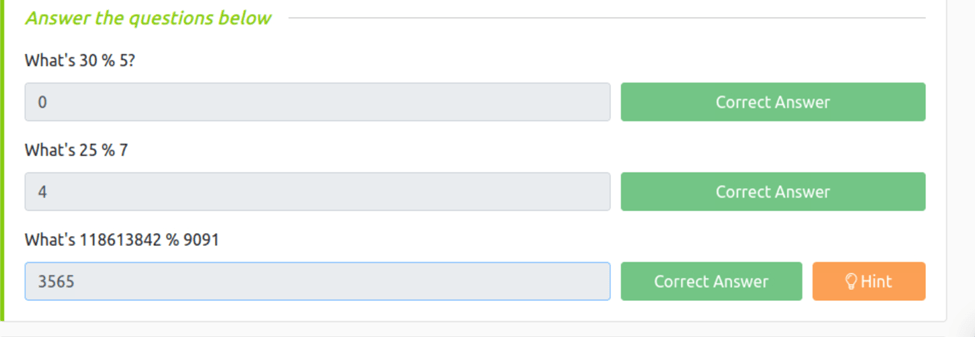
What’s 30 % 5?
Since 30/4=6 with no remainder the anserew is 0
What’s 25 % 7
27/7=3.571 and since it is not evenly divisible the answer is 4 when we round up
What’s 118613842 % 9091
118613842/9091=3565 we get this answer by using the hint that says to use Python. Opening an interpreter shell and plugging in the question it gives us the answer.
Task 5 Types of Encryption
Should you trust DES? Yea/Nay
No DES should not be trusted as it has been broken and the keys only use 56bits.
What was the result of the attempt to make DES more secure so that it could be used for longer?
Just from googling, we can see that triple des was created after des was found insecure.
Is it ok to share your public key? Yea/Nay
Yes, it’s ok to share your public key, as your public key is needed to encrypt stuff being sent to you so you can use your private key to decrypt.

Task 6-RSA – Rivest Shamir Adleman
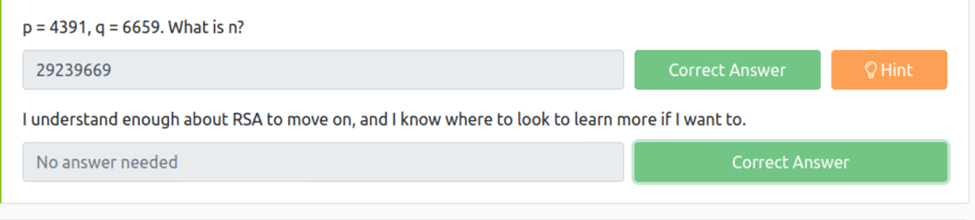
p = 4391, q = 6659. What is n?
from the reading, we know that n is = to the product of p and q so p*q=n which is 29239669
Task 7 Establishing Keys Using Asymmetric Cryptography

Task 8 Digital signatures and Certificates
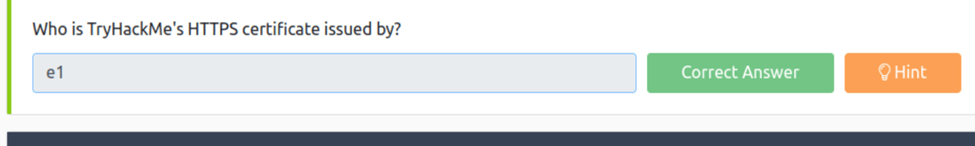
Who is TryHackMe’s HTTPS certificate issued by?
So all we need to do is click on the lock and get to the certificate page and we see the common name is E1 as the issuer.

Task 9 SSH Authentication
What algorithm does the key use?
So from just looking at the file ext we can tel that the key is a rsa key
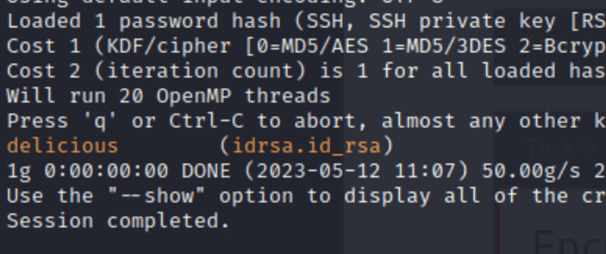
Crack the password with John The Ripper and rockyou, what’s the passphrase for the key?
So for this one, we can just refer to our John room notes and we know we just need to do ssh2john idrsa.id_rsa > idrsa.txt
After we can run John against the .txt file with john –wordlist=/usr/share/wordlists/rockyou.txt idrsa.txt
Which gave us;
Task 10 Explaining Diffie Hellman Key Exchange

Task 11 PGP, GPG and AES
The first thing to do is download the file with the message and the key.
Next is to unzip our file using unzip gpg.zip.
Then we need to import the key into gpg using gpg –-import tryhackme.key
Finally we can run gpg –decrypt message.gpg > message.txt
Which returned;


Task 12 The Future – Quantum Computers and Encryption
