Task 1 John who?
Task 1 is easy just read the material.
Task 2 Setting up John the Ripper
This one is easy as well we can deduce from the reading that its Jumbo John
What is the most popular extended version of John the Ripper?

Task 3 Wordlists
Through reading the given content we can find out the wordlist came from rockyou.com
What website was the rockyou.txt wordlist created from a breach on?

Task 4 Cracking Basic Hashes
Practical
Now you know the syntax, modifiers and methods to crack basic hashes, try it yourself! Download the attached .txt
After downloading the file we can look
What type of hash is hash1.txt?
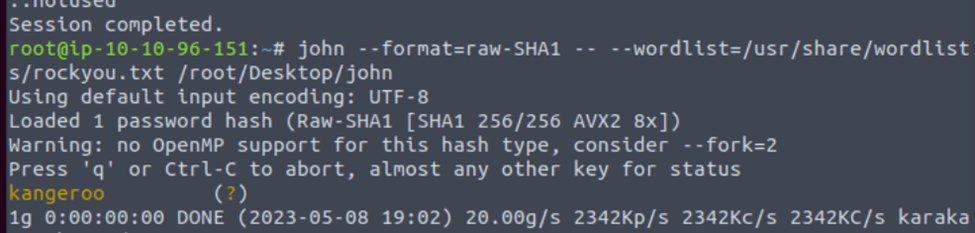
The First thing I Did was open the Kali attack box and download the file. So using the hash-id.py 2e728dd31fb5949bc39cac5a9f066498 we found out that this hash is a md5


What is the cracked value of hash1.txt?
So to crack this hash we can just run # john –format=raw-md5 –wordlist /usr/share/wordlists/rockyou.txt /root/Desktop/john
This returned:

After imputing both answers biscuity was correct

And for the next few questions we will do the same process.
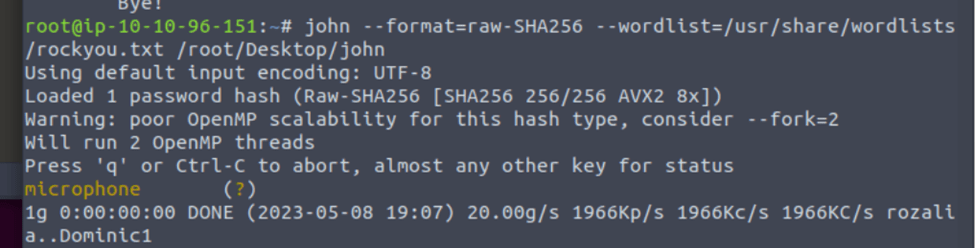
What type of hash is hash2.txt?
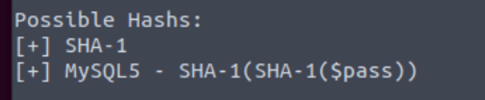

What is the cracked value of hash2.txt

What type of hash is hash3.txt?
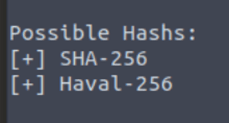

What is the cracked value of hash3.txt

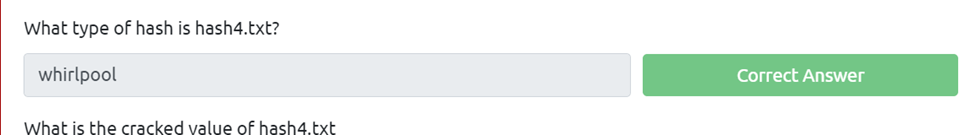
What type of hash is hash4.txt?

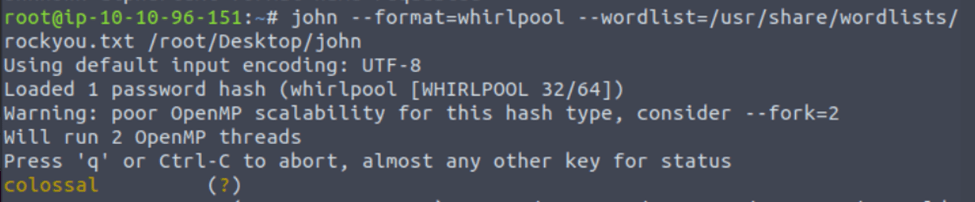
What is the cracked value of hash4.txt

Task 5 Cracking Windows Authentication Hashes
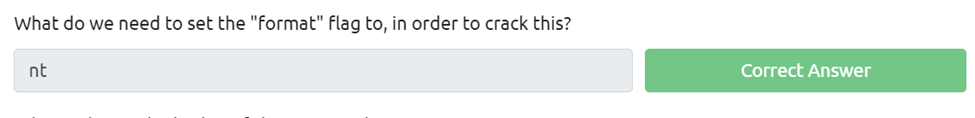
What do we need to set the “format” flag to, in order to crack this?
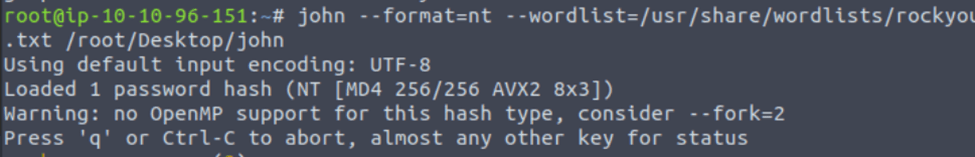
What is the cracked value of this password?

Task 6 Cracking /etc/shadow Hashes
Practical
Now, see if you can follow the process to crack the password hash of the root user that is provided in the “etchashes.txt” file. Good luck!
Answer the questions below
What is the root password?
The first thing to do is create a file and put the first line of the etchashes.txt in it I made it through touch so it looked like.
Touch local_passwd
Than I pasted the root:x:0:0::/root:/bin/bash into the file
Next I created another file for local_shadow
Than put the second line in that file
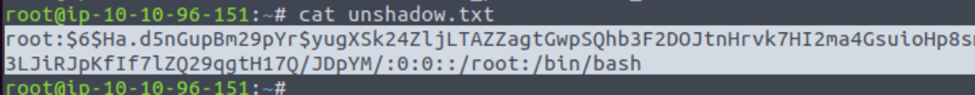
root:$6$Ha.d5nGupBm29pYr$yugXSk24ZljLTAZZagtGwpSQhb3F2DOJtnHrvk7HI2ma4GsuioHp8sm3LJiRJpKfIf7lZQ29qgtH17Q/JDpYM/:18576::::::
next I ran unshadow local_passwd local_shadow > unshadow.txt
Which gave me

I than just ran john /usr/share/wordlist/rockyou.txt /root/unshadow.txt


Task 7 Single Crack Mode
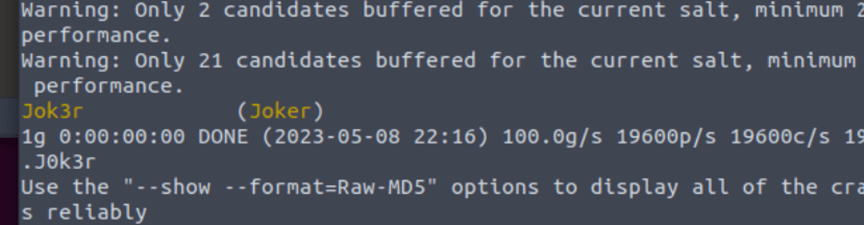
What is Joker’s password?
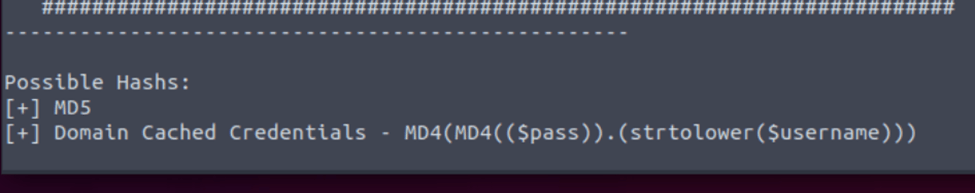
So the first is to run hash-id.py which we find out it’s a md5
And the next thing to do is create a file with the username:hash so we have. Joker: 7bf6d9bb82bed1302f331fc6b816aada
Than we can run
john –single –format=raw-md5 /root/Desktop/john
Which returns
Task 8 Custom Rules
What do custom rules allow us to exploit?
From reading we know we can exploit password complexity predictability
What rule would we use to add all capital letters to the end of the word?
From the reading we know its Az for the original word and then “[A-Z]” to append the capital letters to the end.

What flag would we use to call a custom rule called “THMRules”
Again from the reading it tells us our flag would be –rule=THMRules
Task 9 Cracking Password Protected Zip Files
What is the password for the secure.zip file?
The first thing to do is to get the zip file hash by using zip2john secure.zip > secure.txt
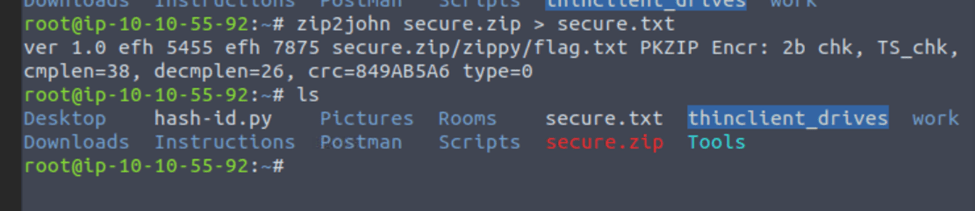
Then we can simply use john to crack the hash using john –wordlist=/usr/share/wordlists/rockyou.txt secure.txt
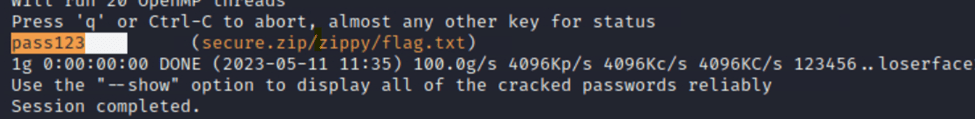

From here we can try to try to open the flag.txt file with pass 123
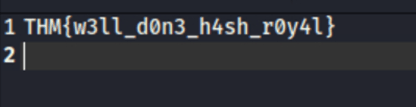
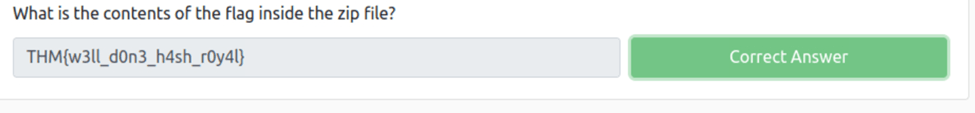
Task 10 Cracking Password Protected RAR Archives
Were going to do the same thing pretty much just using different functions of John
First we run rar2john secure.rar > secure.txt and then ─$ john –wordlist=/usr/share/wordlists/rockyou.txt secure.txt
Then we use a password to open up the .rar file and open up the flag.txt and we get

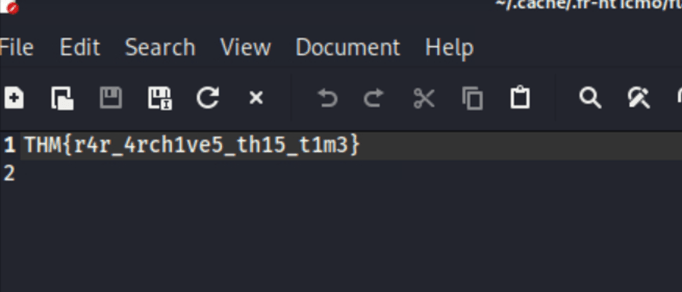

More of the same
What is the SSH private key password?
First we use ssh2john idrsa.id_rsa > idrsa than john –wordlist=/usr/share/wordlists/rockyou.txt idrsa
And we get this

Task 12 Further Reading