Task 1 Introduction to Metasploit
Task 2 Main Components of Metasploit
What is the name of the code taking advantage of a flaw on the target system?
We know that code taking advantage of a flaw is a exploit.
What is the name of the code that runs on the target system to achieve the attacker’s goal?
The name of the code is AKA the payload.
What are self-contained payloads called?
From reading we know singles are self contained.
Is “windows/x64/pingback_reverse_tcp” among singles or staged payload?
We can tell this is a singles payload because of the _ between payback and reverse

Task 3 Msfconsole
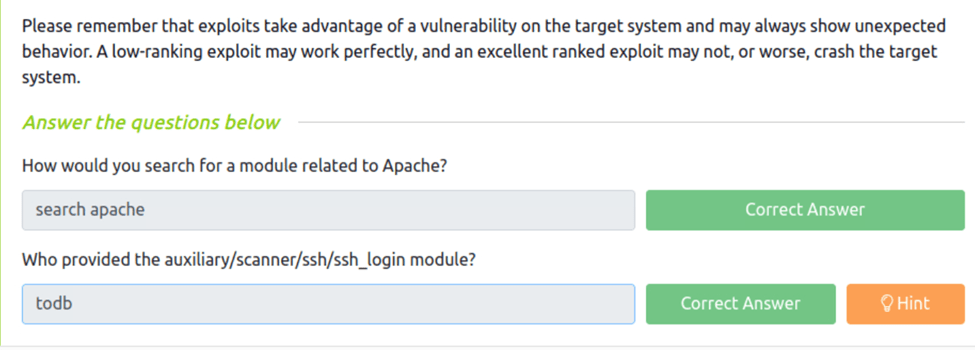
How would you search for a module related to Apache?
From the reading we know the Search apache is the syntax.
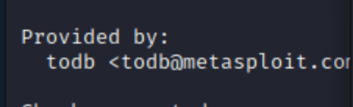
Who provided the auxiliary/scanner/ssh/ssh_login module?
For this one we need to fire up msfconsole and use they syntax info auxiliary/scanner/ssh/ssh_login which returns
Task 4 Working with modules
How would you set the LPORT value to 6666?
To set lport we just use the syntax set lport 6666
How would you set the global value for RHOSTS to 10.10.19.23 ?
To globally set a rhost we would use the syntax setg rhost 10.10.19.23
What command would you use to clear a set payload?
We would just invoke the unset payload command
What command do you use to proceed with the exploitation phase?
From the reading we know we would use the exploit command

Task 5 Summary