Task 1 What is an SSRF?
What does SSRF stand for?
From our reading we know its server side request forgery
As opposed to a regular SSRF, what is the other type?
We know this is blind

Task 2 SSRF Examples
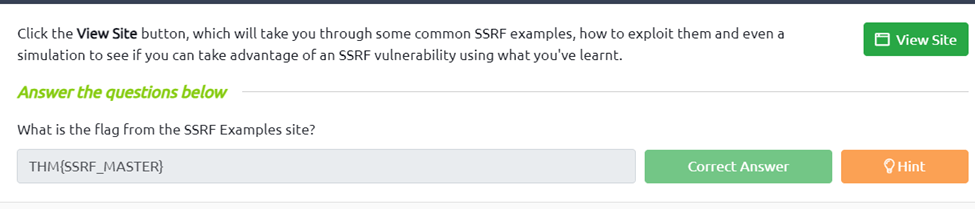
What is the flag from the SSRF Examples site?
First we go to the visit site and read through the documentation. Now we get to the last page and we have a URL https://website.thm/item/2?server=api but we would like it to call data from our server at https://server.website.thm/flag?id=9. So the first thing we must do is eliminate the =api from the URL also the https:// form our server address. Next, we concatenate them to get https://website.thm/item/2?server= server.website.thm/flag?id=9 and if we run that we get a error 509 this is because its still trying to server the website after ours so got fix this we do “&x=” to prevent the remaining part of the path from being appended.
Task 3 Finding an SSRF
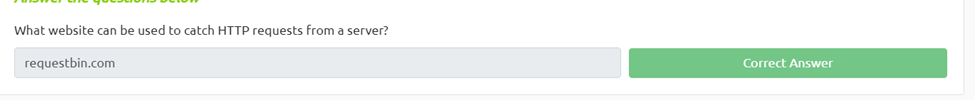
What website can be used to catch HTTP requests from a server?
From the reading we can see requestbin.com but I think Burp would be better suited.
Task 4 Defeating Common SSRF Defenses
What method can be used to bypass strict rules?
From reading we see open redirects could bypass stringent rules
What IP address may contain sensitive data in a cloud environment?
169.254.169.254
What type of list is used to permit only certain input?’
Allow list
What type of list is used to stop certain input?
Deny list

Task 5 SSRF Practical
What is the flag from the /private directory?
To get this flag we just need to follow the instructions. First create an account and navigate to the new-account-page. Now we can start to mess with the avatars because if you look in the source code the avatars are coming from a URI so we can now open our inspector by right clicking on the little circle below the avatar, and change the value of a avatar to private and updating the avatar. We get an error because the private folder is on a deny list but using directory traversal we can set the value to x/../private and clicking update avatar. Now the avatar should be blank but if you looking the source code we now get a base64 behind our URI which is much shorter than the original. If we decode this with base64 decode we get our flag.